搜索结果: 1-15 共查到“安全科学技术 Security”相关记录15条 . 查询时间(0.172 秒)
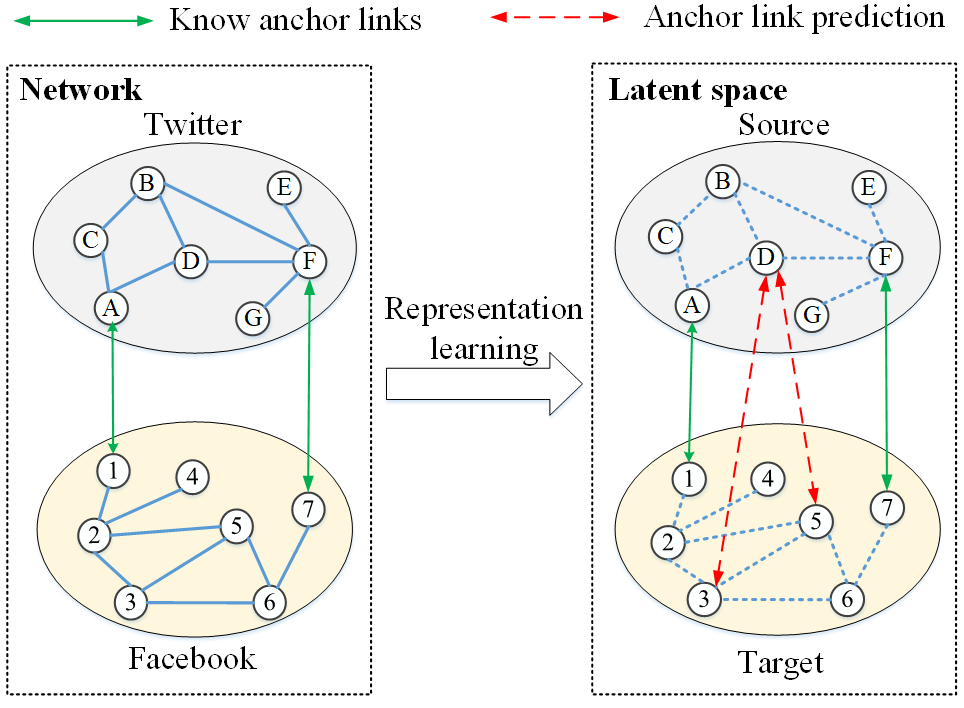
哈尔滨工程大学计算机科学与技术学院师生在网络与信息安全领域顶级国际期刊IEEE Transactions on Information Forensics and Security发表论文(图)
信息安全 IEEE Transactions on Information Forensics and Security 社交网络 取证
2024/7/14
[成果]天津师范大学心理学部杨海波教授课题组的论文“The influence of subjective value on mobile payment security warnings: An eye movement study”在Displays发表
警示信息 规避风险交易 眼动追踪技术 人机交互
2024/3/27
雷速共建数据
由天津师范大学心理学部杨海波教授(通讯作者)和博士生杜宇菲(第一作者)共同撰写的论文“The influence of subjective value on mobile payment security warnings: An eye movement study”在Displays发表。该论文得到国家自然科学基金项目(32271140)的资助支持。
南开大学计算机学院刘哲理教授数据安全团队再中USENIX SECURITY信息安全顶级会议
南开大学计算机学院 刘哲理 数据安全 USENIX SECURITY 信息安全 网络安全 安全多方计算
2022/5/13
第九届中国信息安全博士论坛(2016China Information Security Doctor Conference,CISDC2016)将于2016年8月在吉林举办。论坛由教育部高等学校信息安全专业教学指导委员会指导,中国信息安全博士网主办,北京艾得威尔信息咨询中心承办。

Experts identify easy way to improve smartphone security(图)
smartphone security Experts identify
2014/12/1
What information is beaming from your mobile phone over various computer networks this very second without you being aware of it?
Experts say your contact lists, email messages, surfed webpages, brow...
HKS Security Experts Respond to President Obama's ISIS Strategy
President Obama's ISIS Strategy security
2014/9/12
Following President Obama’s September 10 speech to the nation proposing a strategic response to the Islamic State in Iraq and Syria (ISIS/ISIL), several Belfer Center for Science and International Aff...
孟加拉国和平与安全研究所(Bangladesh Institute of Peace and Security Studies,BIPSS)
孟加拉国和平与安全研究所 Bangladesh Institute of Peace and Security Studies BIPSS
2013/12/3
Bangladesh Institute of Peace and Security Studies (BIPSS) is a leading institution in Bangladesh for informed analysis on all aspects of broad spectrum of peace and security studies in the region and...
亚洲非传统安全研究协会(The Consortium of Non-Traditional Security Studies in Asia)
亚 洲 非 传 统 安 全 研 究 协 会 The Consortium of Non-Traditional Security Studies in Asia
2013/12/3
The Consortium of Non-Traditional Security Studies in Asia (NTS-Asia) marks the 3rd phase of the Ford-RSIS Project on Non-Traditional Security Issues.
The project is funded by the Ford Foundation, an...
Data survivability vs. security in information systems
Data survivability Data security Protection Redundancy Attack Optimization
2012/4/16
A multiple objective problem formulation and solution methodology is presented to select optimal information and data storage configurations considering both data survivability and data security, as w...
A game theoretic framework for evaluation of the impacts of hackers diversity on security measures
Security Modelling Quantitative security evaluation Markov chains Game theory
2012/4/22
Game theoretical methods offer new insights into quantitative evaluation of dependability and security. Currently, there is a wide range of useful game theoretic approaches to model the behaviour of i...
The Fifth International Conference on Information Assurance and Security (IAS09)(第五届信息保障与安全国际会议(IEEE CS))
第五届 信息保障与安全 国际会议
2009/4/3
IEEE Second International Symposium on Electronic Commerce and Security(第二届电子商务与安全国际研究会)
第二届 电子商务 安全
2009/4/3


